It was 3:32 AM when an automated alert landed in our inbox. It was from the Netcraft Takedown Service, and the subject line was stark: “Malicious web shell being hosted on your network.” This is the kind of notification that sets alarm bells ringing for any hosting provider.
For those unfamiliar, Netcraft is not just any company; it’s a world leader in cybercrime detection, disruption, and takedown services. They are trusted by some of the largest global brands, including Microsoft and Meta.
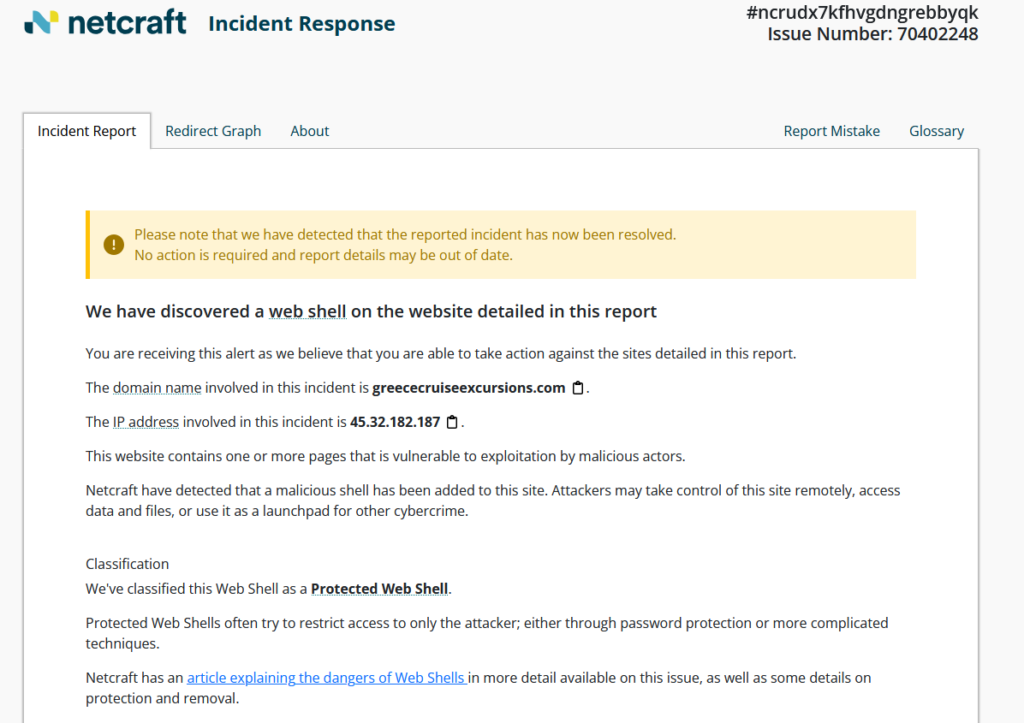
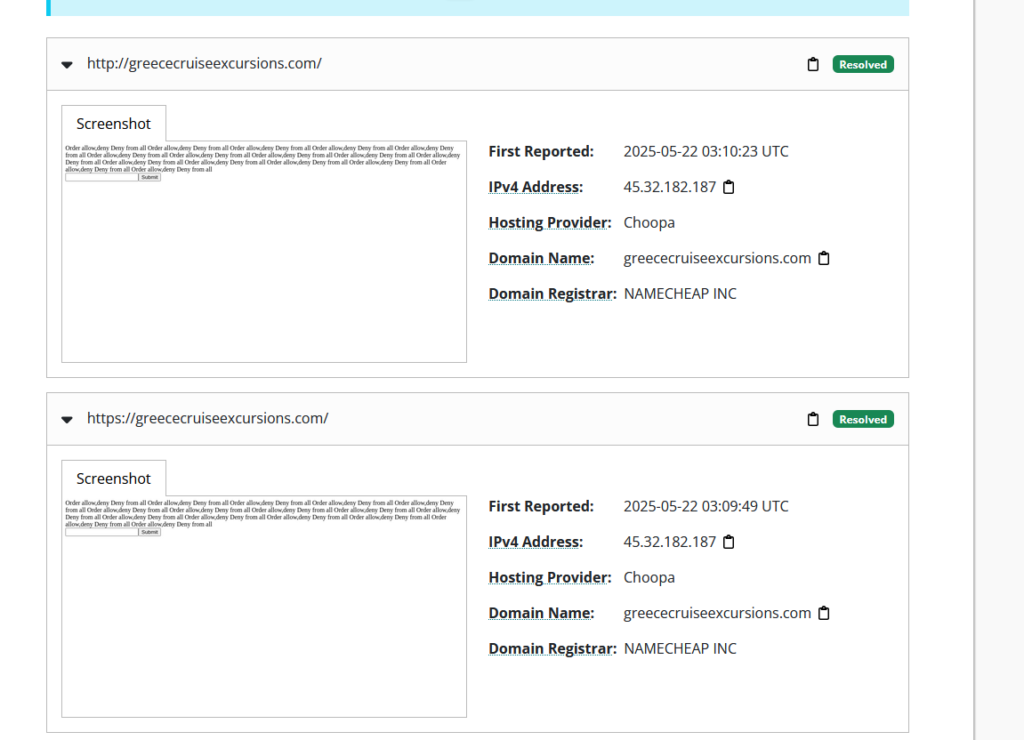
The report identified a malicious web shell on a client’s website, greececruiseexcursions.com. It went on to explain that once a web shell is in place, an attacker can upload files, execute commands on the server, and even use the server to send spam.

This client wasn’t using our SpeedFirst WordPress Hosting -where performance is the top priority, and security is the zeroth; built in from the ground up. Their WordPress installation was directly exposed to the internet, making it a target for automated hack attempts. We immediately took action and contacted our client.
While the situation was critical, the good news is that a hacked WordPress website can be cleaned and restored. If you’re wondering how to recover a hacked website, read on.
Another Common Threat: SEO Spam and Ranking Damage
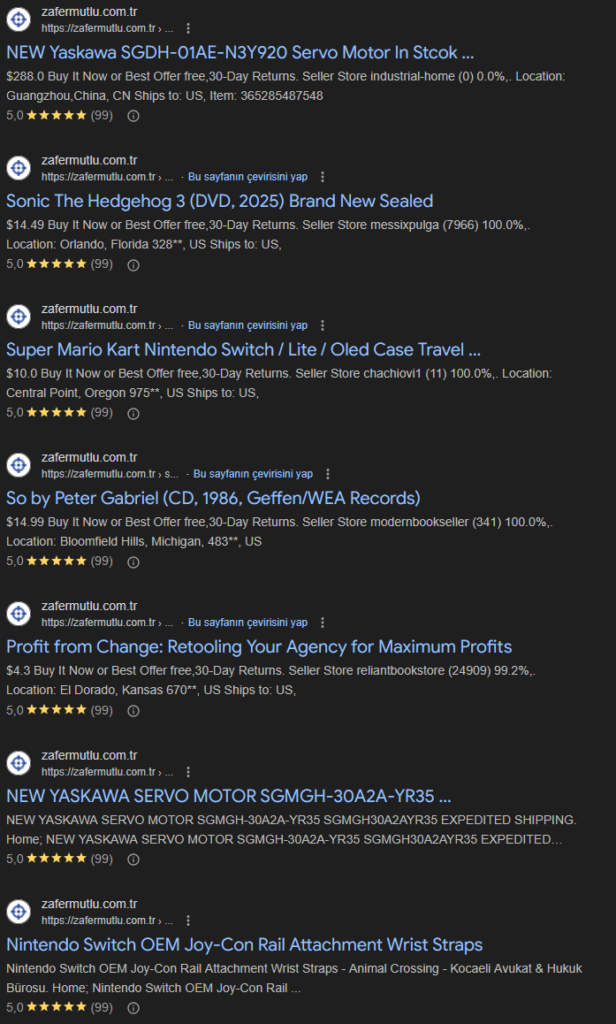
While a web shell is a direct server-level threat, another insidious type of hack targets a brand’s reputation directly on Google. This is exactly what happened to another client of ours, a reputable law firm at zafermutlu.com.tr. Their site fell victim to a devastating SEO spam attack.
In this scenario, the hackers didn’t deface the homepage. Instead, they quietly added thousands of hidden spam pages promoting illicit products. The real damage occurred when Google discovered and indexed these pages. Suddenly, the law firm’s official search results were filled with this spammy, irrelevant content. This not only destroyed their hard-earned search engine rankings but also severely damaged the professional trust essential for a law practice. The firm didn’t realize what was happening until their organic traffic plummeted and their online reputation was at risk.
Whether your site is compromised by a technical web shell, like our first example, or a reputation-damaging SEO spam attack like the one faced by zafermutlu.com.tr, the recovery process requires a methodical approach. The following steps will guide you through cleaning your site and reclaiming your digital presence.
Step-by-Step Guide to Learn How to Recover Hacked Websites
If you discover your website has been hacked, follow these steps methodically to regain control and secure your site.
Step 1: Isolate Your Website
Immediately take your site offline. This prevents attackers from causing more damage, stops malware from spreading to your visitors, and protects your brand’s reputation. You can do this by using a maintenance mode plugin or by replacing your index.php file with a temporary, static index.html page. This is the first step in learning how to recover hacked websites.

Step 2: Backup Your Hacked Site
This might sound counterintuitive, but you must create a full backup of the current, compromised website (both files and the database). This backup is a critical piece of evidence. It will allow you to analyze the hack without touching the live server and ensure you don’t accidentally delete important data during the cleanup process.
Step 3: Scan WordPress For Vulnerabilities
With your site offline, perform a thorough scan. You must scan WordPress for vulnerabilities thoroughly to identify infected files and scripts. Use a combination of tools:
- Server-Side Scanners: Ask your host if they have tools like ClamAV.
- External Scanners: Use services like Sucuri SiteCheck or Wordfence to scan your site from the outside.
- Plugins: Install a security plugin on your backed-up copy to perform a deep scan of files and the database.
These scans will generate a list of suspicious files, malicious code injections, and known vulnerabilities.

Step 4: Remove Malware from WordPress Website and Clean Your Files
This is the most hands-on part of the process.
Replace Core Files: Download a fresh copy of WordPress from WordPress.org.
- First, delete your site’s old
wp-adminandwp-includesdirectories. You should also delete all other core WordPress files from your root directory (likewp-login.php,wp-mail.php, etc.). Do not delete yourwp-contentfolder andwp-config.phpfile. - Next, upload the new
wp-adminandwp-includesdirectories and all other files from the fresh WordPress download into your site’s root directory. -
Handle
wp-config.phpwith care: This file contains your database information but can also be infected. To be safe, do not reuse your old file directly. Instead, find thewp-config-sample.phpfile from the new download. Open it, and carefully copy your database details (DB_NAME, DB_USER, DB_PASSWORD, DB_HOST, and table prefix) from your oldwp-config.phpfile into it. Save this new file aswp-config.php.
Inspect wp-content: Go through your wp-content folder file by file. This is where most hacks hide. Delete any suspicious-looking plugins or themes.
Reinstall Plugins and Themes: Delete all of your plugins and themes. Reinstall them from their official sources (the WordPress repository or the developer’s official website). Never use a version from an unknown source.
Check .htaccess: Since you have already created a clean wp-config.php, now focus on your .htaccess file. Carefully inspect it for any malicious code or strange redirect rules. Compare it with a default WordPress .htaccess file for reference.
Step 5: Clean Your Database
Hackers can also inject malicious content and spammy links into your database. Use a tool like Search-Replace-DB or a security plugin’s database scanner to look for suspicious content (like script tags or spam keywords) within your posts, pages, and comments. Remove any malicious entries you find. This complements your website security check and reinforces your recovery.

Step 6: Change All Your Passwords and Secrets
Assume that the attacker has stolen every password. You must change everything:
- All WordPress user passwords (especially for admin accounts).
- Database password.
- Hosting control panel (cPanel/Plesk) password.
- FTP/SFTP passwords.
- Go to the official WordPress salt generator and replace the old keys in your wp-config.php file. This will log out all users and invalidate existing cookies.
Step 7: Bring Your Site Back Online
Once you have uploaded the clean files and the sanitized database, remove the maintenance page to bring your site back online. Clear all server-side and browser caches. Confirm that your website security check passes before going live again. You’re now close to fully completing your how to recover hacked website process.
Step 8: Monitor Closely
Keep a close watch on your site for a few days. Check your logs and use a file integrity monitor to ensure the attacker doesn’t return using a backdoor you might have missed.

After the Cleanup: Removing Spam Pages from Google
Once you’ve followed Steps 1-8 and your website is clean, the job isn’t over—especially if you were a victim of an SEO spam attack like zafermutlu.com.tr. You must now tell Google to remove the malicious pages from its search results. Here’s how to handle the cleanup.
Step 1: Confirm the Spam Pages are Gone
Before asking Google to do anything, double-check that the spam URLs are actually removed from your server. When you visit one of the bad URLs, it must return a “404 Not Found” or “410 Gone” error. This is critical. If the pages still exist, Google won’t remove them.
Step 2: Find All Indexed Spam URLs
Go to Google and use the site: search operator to find all the pages Google has indexed for your domain. Look for anything that doesn’t belong.
- Search for:
site:yourdomain.comto see everything.
Compile a list of all the spam URLs you find.
Step 3: Request Removal in Google Search Console
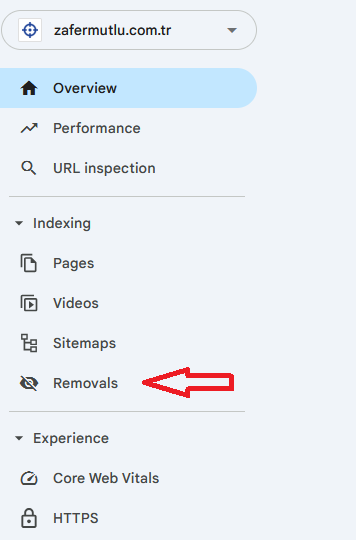
Use the list you compiled to ask Google for a temporary removal. This is the fastest way to get the spam out of search results while you wait for Google to re-crawl your site naturally.
- Log in to Google Search Console.
- Go to the “Removals” tool in the left-hand menu.
- Click “New Request” and enter each spam URL one by one. Choose the “Remove this URL only” option.
This will hide the URLs from search results for about six months, which is plenty of time for Google to see that the pages are permanently gone (because they return a 404 error) and remove them from the index for good.
Step 4: Disallow Google Access to Removed Pages
After making sure the spam pages do not show up in your search results, add Disallow rule for those pages in your robots.txt file to make sure Google do not crawl the pages again.
The Proactive Solution: Prevention Over Cure
Cleaning a hacked site is a reactive, time-consuming, and stressful process. The client in our story was able to recover, but they experienced downtime and a major security scare. What if you could prevent this from ever happening in the first place?
This is where our hosting philosophy makes a difference. Speedfirst WordPress Hosting is built not just for speed, but on security. Security isn’t an add-on, it’s the zeroth priority; deeply integrated into the core infrastructure. That’s why it dramatically lowers the risk of intrusion, so you won’t have to constantly scan WordPress for vulnerabilities, run emergency website security checks, or figure out how to recover hacked websites content under pressure.

SpeedFirst fundamentally changes how your site is exposed to the internet, reducing attack surfaces and preventing unauthorized access. You don’t just react and remove malware from WordPress website infrastructure; you block those threats entirely.
We convert your WordPress site into a static-like infrastructure. Your visitors interact with an ultra-fast, read-only version of your site, making it impossible for attackers to exploit common WordPress vulnerabilities. The actual WordPress core, with its admin dashboard and database, is completely locked down and firewalled, accessible only to you when you need to make updates.
Here are the benefits:
- Complete Prevention of Hacking Attempts: It is designed to completely prevent hacking attempts like the web shell incident mentioned earlier. Nobody can access your WordPress core if you don’t want them to, meaning there’s no need to constantly scan WordPress for vulnerabilities or figure out how to recover hacked website content later.
- No More Update Anxiety: Forget about your site breaking on WordPress updates. Since the public-facing site is separate, updates can be tested in a safe environment without affecting your visitors.
- Eliminate Risky Security Plugins: Security plugins can be complex and, ironically, can sometimes introduce vulnerabilities themselves. Our service removes this dependency entirely, offering you secure WordPress hosting that works by design, not patchwork.
- Automated Defense: Our system automatically blocks hacking attempts and malicious bots before they can even reach your WordPress installation. With continuous monitoring and built-in protection, you dramatically reduce the chances of needing to remove malware from WordPress website files or troubleshoot how to recover hacked website data.
Understanding how to recover hacked website is crucial, but preventing the issue matters even more. If you’re already dealing with a compromise, follow the guide above to remove malware from WordPress website, run a full website security check, and scan WordPress for vulnerabilities using multiple methods.
Next time, don’t wait for a disaster to happen. Move to a platform that provides true secure WordPress hosting. With our SpeedFirst WordPress Hosting, you can lock down your site at the infrastructure level, and never need to worry about how to recovering hacked websites again.
